 |
| Music |
| Computing |
| Android |
| Ref Library |
| Download |
| Built |
| Blue Sky |
| Info Arch |
House Network
Here at Tsort Turret we need a reasonably complex network configuration to do all that is required. This is shown in the figure above. Our needs (in order of importance) were:
- Security: We wanted to be able to rely on the security of the network
- Configuration: We have always run the network with rules about which machines can do what. For example the children's machine is upstairs and unsupervised, so we don't allow it any access to the internet
- Services: Anything connecting to the network requires a range of services from DHCP, mail, domain name lookup, printers, shared directories and internal web sites to control devices
- Always On: We need various services to be accessible at all times
- Web Server: Our web server provides roaming access and has to be available at a fixed address and 24 hours a day
- Silent: The infrastructure must run quietly, we used (from 1993 to 2006) to the control the network using an old PC, the level of constant noise just got too much
- Guests: Visitors often need to be able to connect to the internet, we want to allow them to, without exposing our own computers to unreasonable risk
- Cost: We are cheap, most of the computers have been inherited from relations that upgraded to systems that are able to run Vista. We still have one machine running Windows 98 and our most recent purchase was more than two years ago
Our approach to this list of requirements was to create a network like this:
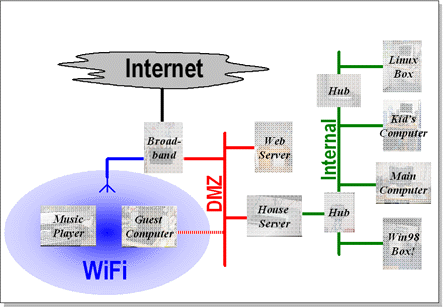
- Security: Not one but two firewalls
- Configuration: The house server controls access into and out from the internal network
- Services: The house server provides most of the services
- Always On: The broadband connection provides the link, the house server provides the services
- Web Server: A seperate server (in the stables) provides web services
- Silent: Unbelievably quiet
- Guests: Visitors connect to the less secure network
- Cost: Reasonable (not dirt cheap)
Firewalls
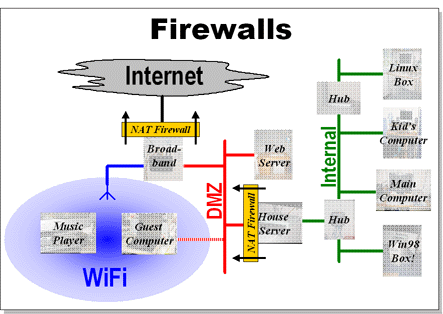
The network has two seperate NAT (network address translation) firewalls. Facing the internet is the broadband router supplied by our internet service provider. This provides a wireless network (WiFi) that is protected by WEP encryption and a number of wired Ethernet ports. The firewall is managed via web pages, so for example it knows to map all in-bound requests on port 80 to the web server.
The wired network behind the router is known as the "DMZ" (De-Militarized Zone), it has an address in the 192.168.*.* address space (something like 192.168.2.*). The WiFi network also has its own unique address space (like 192.168.1.*)
However, WEP encryption has been broken, the internal workings of the broadband router are closed and we are running a publicly accessible web server so there are a number of ways that a potential intruder could get on to the DMZ network. So we have a second NAT firewall on the house server that protects the internal network (192.168.3.*) where most of the computers in the house live. This firewall is running a trusted OS (Linux) and so can be configured to do whatever we want.
Types of client
The level of access that the house server allows depends on which category of client machine it has. There are basically three types of machine on the internal network:
- Completely Trusted: Machines that are known and are in locations where access can be supervised
- Partially Trusted: Machines that are known but are in locations where access is not supervised
- Unknown: Machines that are new to the internal network
Machines are registered in the house server, this is also where they can be switched between being trusted or not trusted. The behaviour of the firewall is controlled by a complex script (that defines the iptables), however to simplify the configuration and ensure that it is consistent all the attributes are defined in a special Perl module that is used by scripts to control the settings.
Unknown
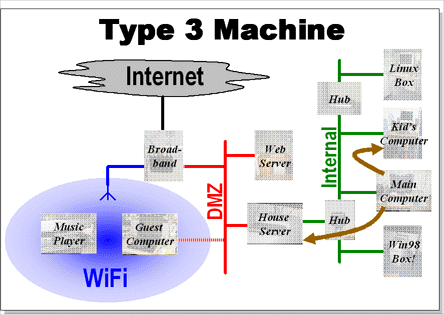
Any machine that is new to the house server is only allowed access to the local subnet. They can connect to the other internal machines (provided the user can logon) but they cannot access even the machines on the DMZ.
Partially Trusted
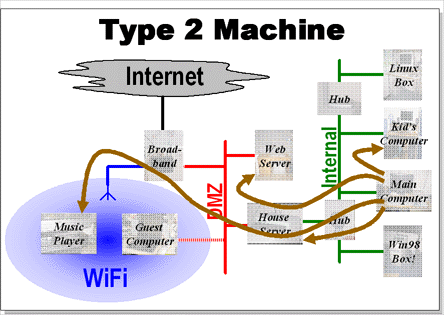
Known but unsupervised machines can access services on the DMZ (and across the WiFi) but cannot see the internet.
Trusted
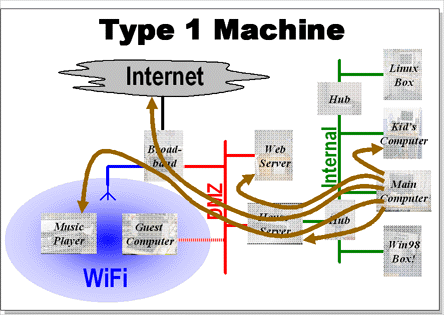
Trusted machines can access anywhere, they route through the two firewalls to connect to the internet.
Guest Access
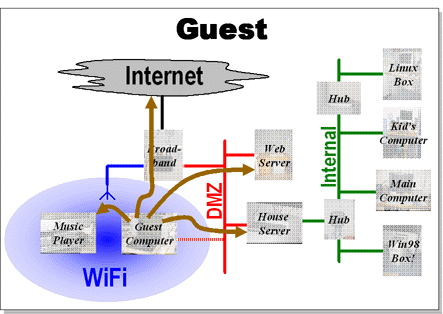
Guest machines do not connect through the house server. Any unknown machine that connects to the WiFi (using the WEP key) or to one of the wired Ethernet access points, has access to all the machines on the unsecured network and unlimited access to the internet. They cannot, of course, access anything on the internal network.
Web Server
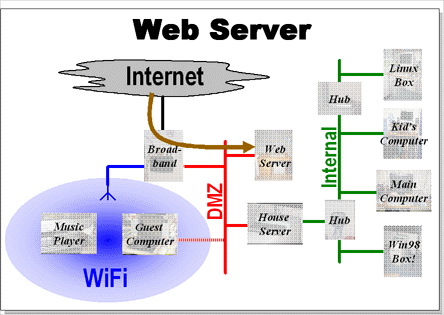
In many ways the web server is like a guest machine. Of course most of the time it is responding to requests from the internet that the broadband router has redirected to it. However even if it did start making requests it would be limited to the unsecured network.
The web server is currently implemented as a headless Linux box. It is running Apache 2.0 and despite the fact that it is an old Pentium-I machine is well able to manage the load (given the limits that my bandwidth imposes I am not worried about the speed of the web server box).
Services
DHCP
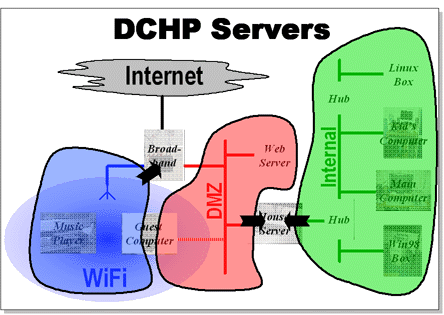
Dynamic Host Control Protocol (DHCP) is the way that computers obtain an IP address when they connect to a network. The broadband router allocates addresses on the WiFi network. The house server provides DHCP services for the wired networks (DMZ and Internal). For machines that the house server knows about the addresses are static, for unknown machines there is a block of addresses (1-149) that are each allocated for limited ammounts of time.
The configuration files in the house server assign a number in the range 150-254 to every computer that is known about. When a known MAC address requests an IP its number is used as the final digit, the first three come from the network's number. There are few enough known computers for there to never be an issue with running out of slots.
DNS
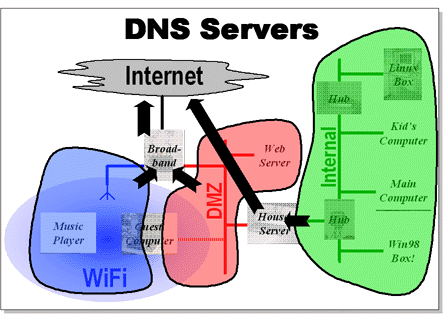
The Domain Name Server (DNS) lookups are also split into two. This time however the DMZ network and WiFi send all requests to the broadband router. This just forwards requests to a suitable system on the internet.
The Internal network is much more interesting. In the configuration for the house server there is a new top level domain (called tsort-turret) so that a number of machines on the internal network and DMZ can be referred to by names like wolf.tsort-turret, tiger.tsort-turret and so on. The BIND server passes DNS requests to an external name server if the requested lookup is not in the tsort-turret domain, it caches these values.
Shared Directories
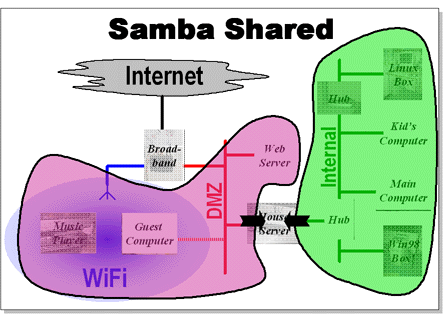
The house server implements Samba to provide services to Microsoft Windows based machines. There are two different types of shares, some are available to any machine on the house networks. These are mostly read-only directories and locations for intermediate storage of backups.
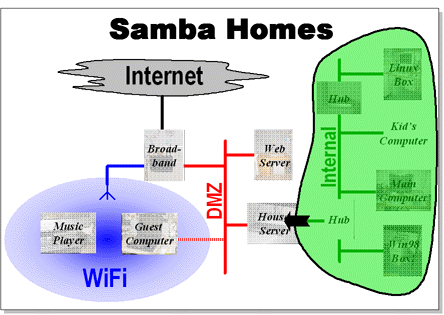
The other SMB directories are the home accounts, these are only visible from the Internal network.
Music
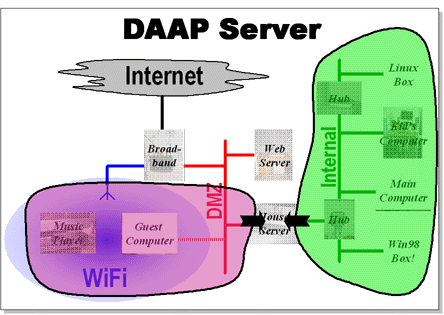
One of the most frequently used services the house server provides is to act as a DAAP server for the house networks, DAAP is the protocol used by iTunes to share access to music. So any iTunes clients can see and play music from the shared collection. This is implemented with the fantastic FireFly server. Most of the clients are not iTunes based (because most of us have MP3 players that are not iPods), we use clients like "Get It Together".
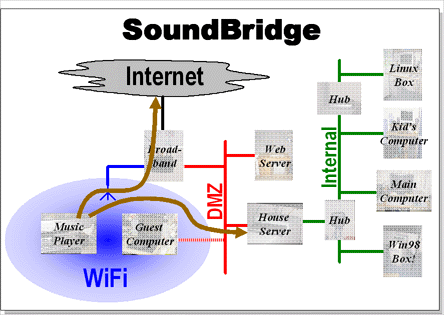
One common way that music is played is via the Roku SoundBridge in the sitting room. The SoundBridge is a great piece of kit, it links to the WiFi and either acts as a client to the DAAP server or plays Internet radio stations. It is plugged in to the HiFi, assuming you can call a 30 year old amplifier and speakers a HiFi.
Other Services
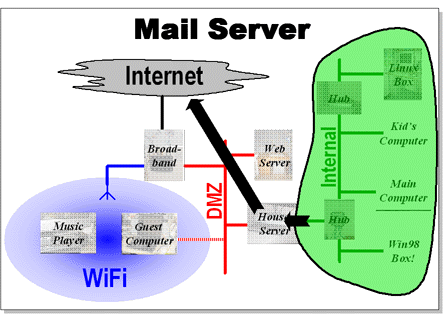
The house server supplies all the other essential services, for example using fetchmail to obtain mail every 5 minutes and an exim configured to deliver it to all the users (after filtering out spam using a Baysian filter). It shares the network time, performs authentification and a variety of other services.
House Server
The house server is implemeneted using a Soekris box. This is a great little computer that is about the size of a thick paperback, runs totally silently and never seems to warm up to room temperature. More details are here.